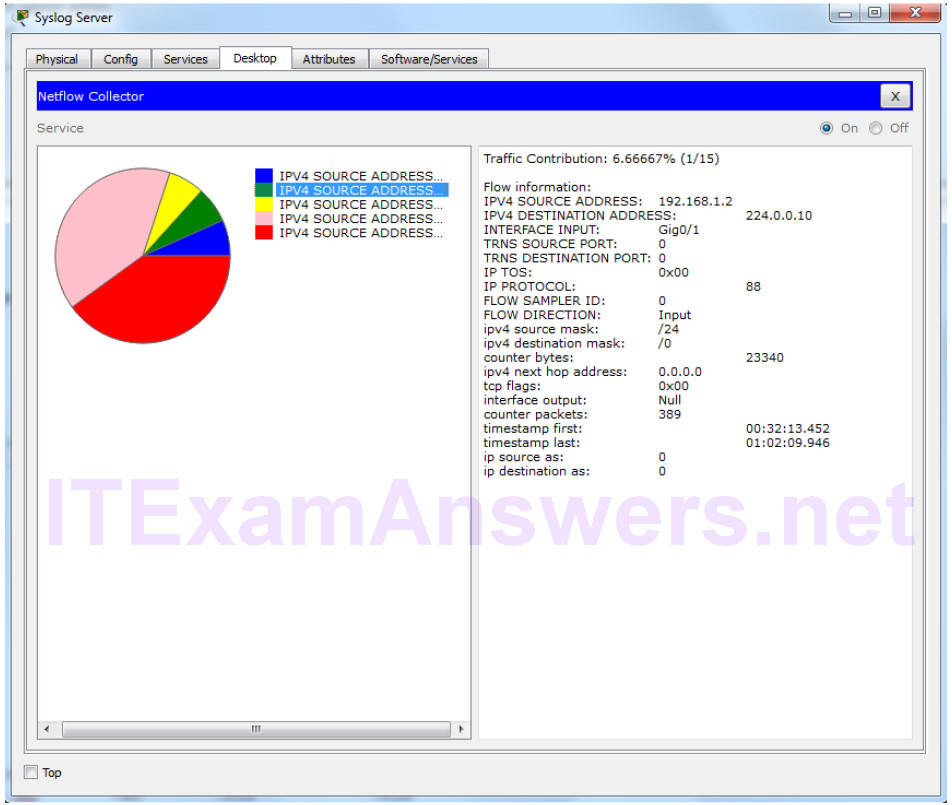
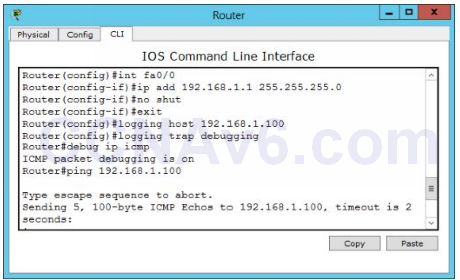
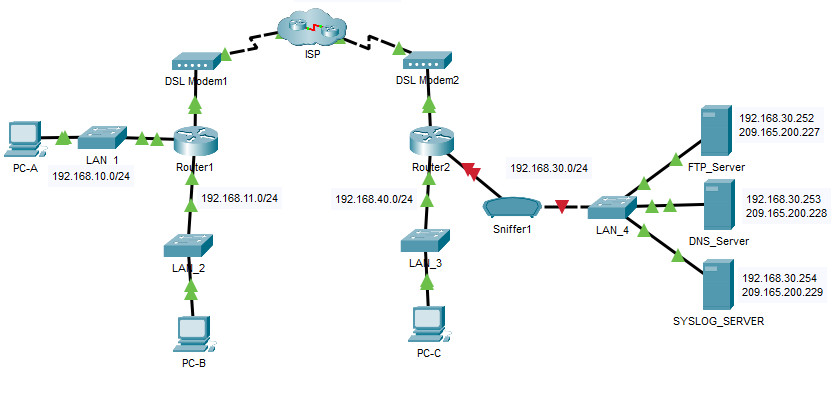
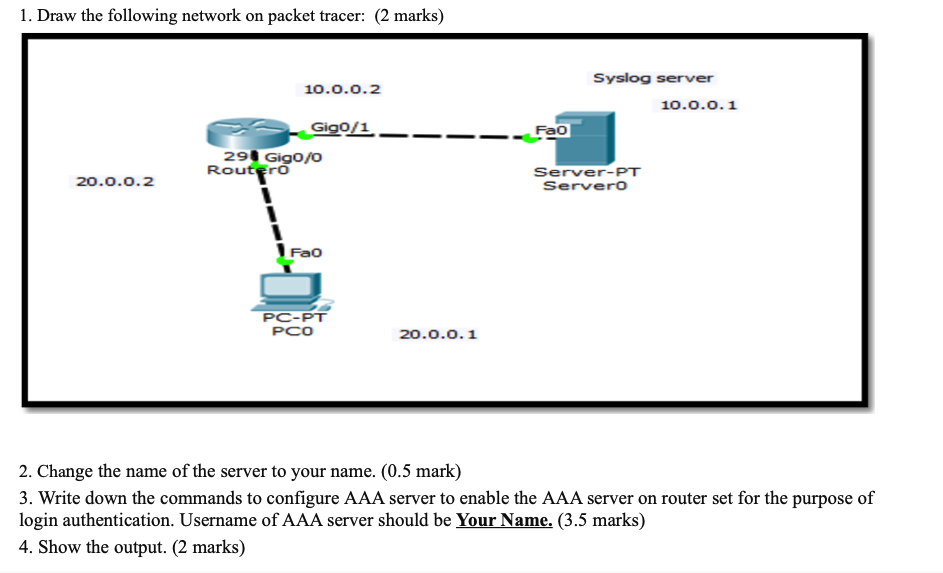
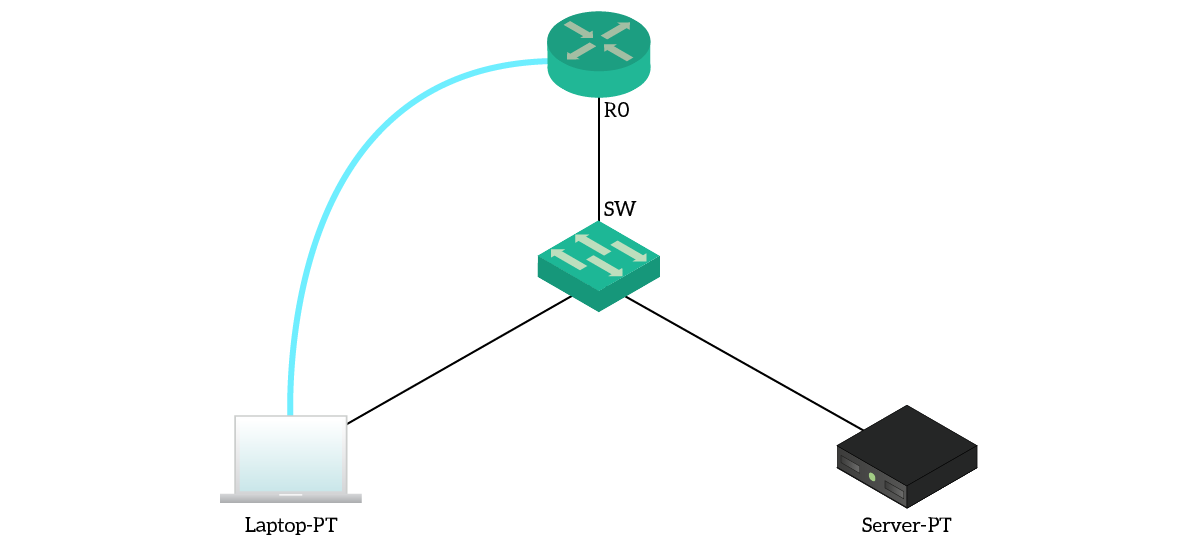
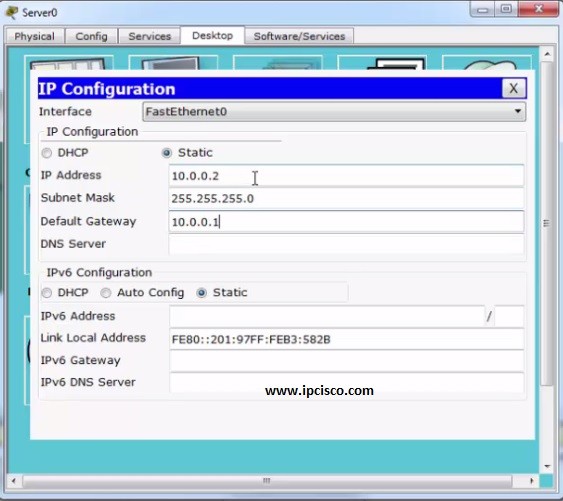
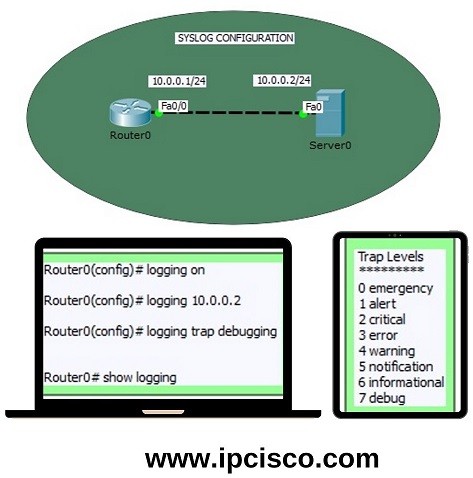
How To Configure NTP And SYSLOG Server - CCNA Windows Ethical Hacking Linux Networking Security Cyber Security Virtualization Cryptography

المواطنين من كبار السن البلد التي تنتمي لها مقابلة tftp server with router config cisco packet tracer - rise-association.com
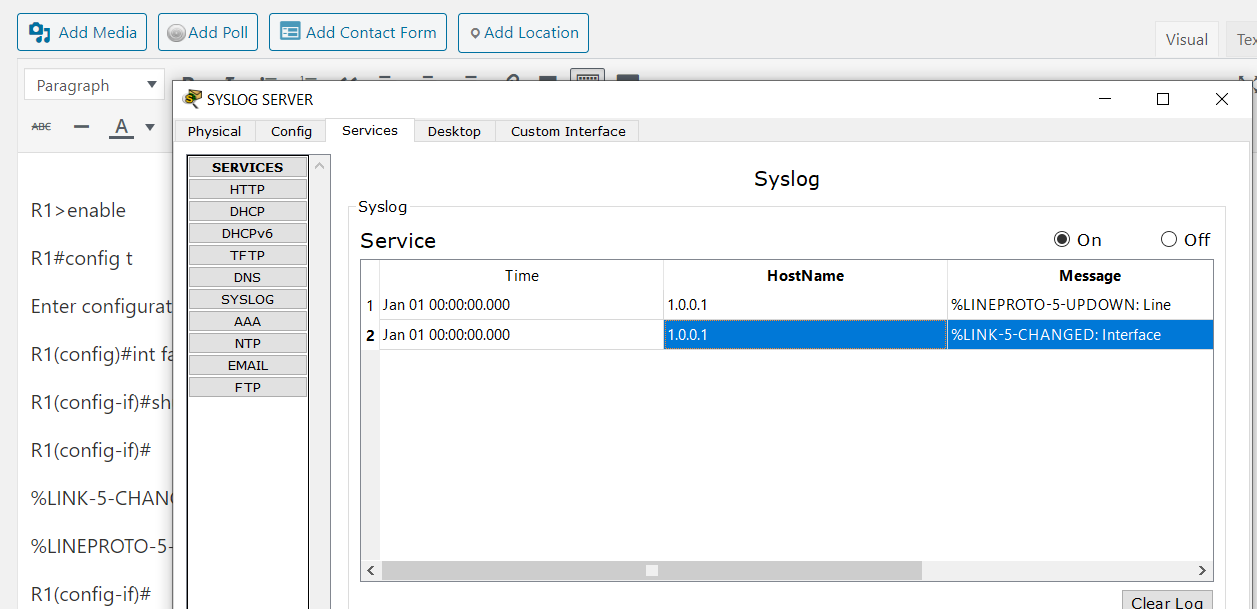
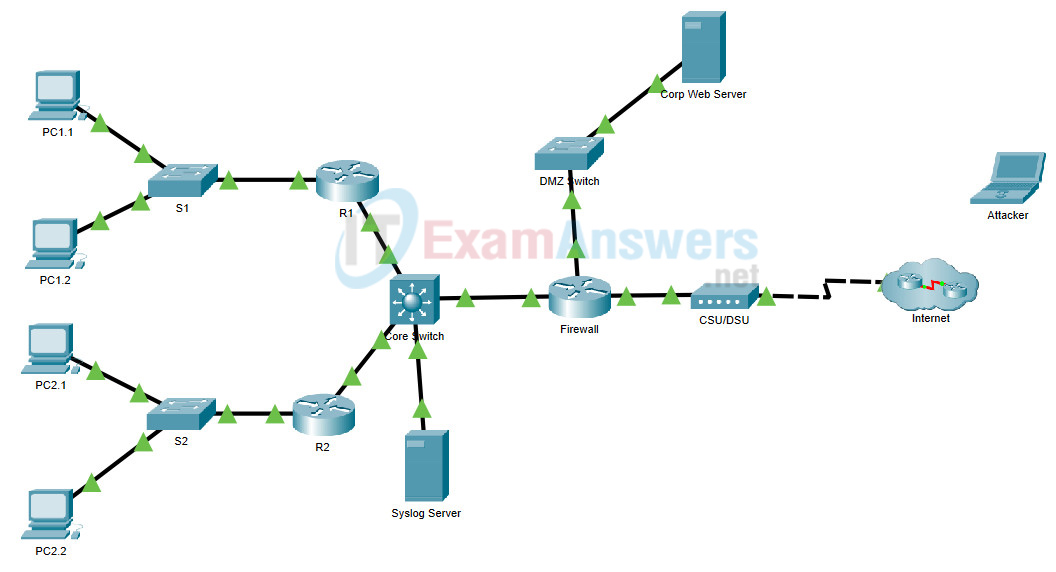
Syslog(log server) and NTP(Time Server):Cisco Packet Tracer Configuration lab | Learn Linux CCNA CEH IPv6 Cyber-Security Online

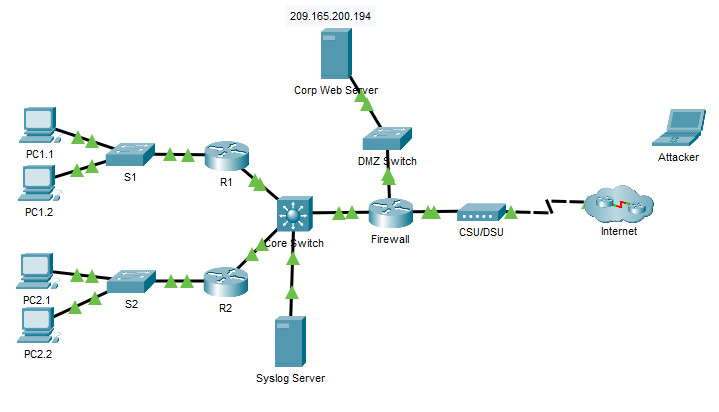
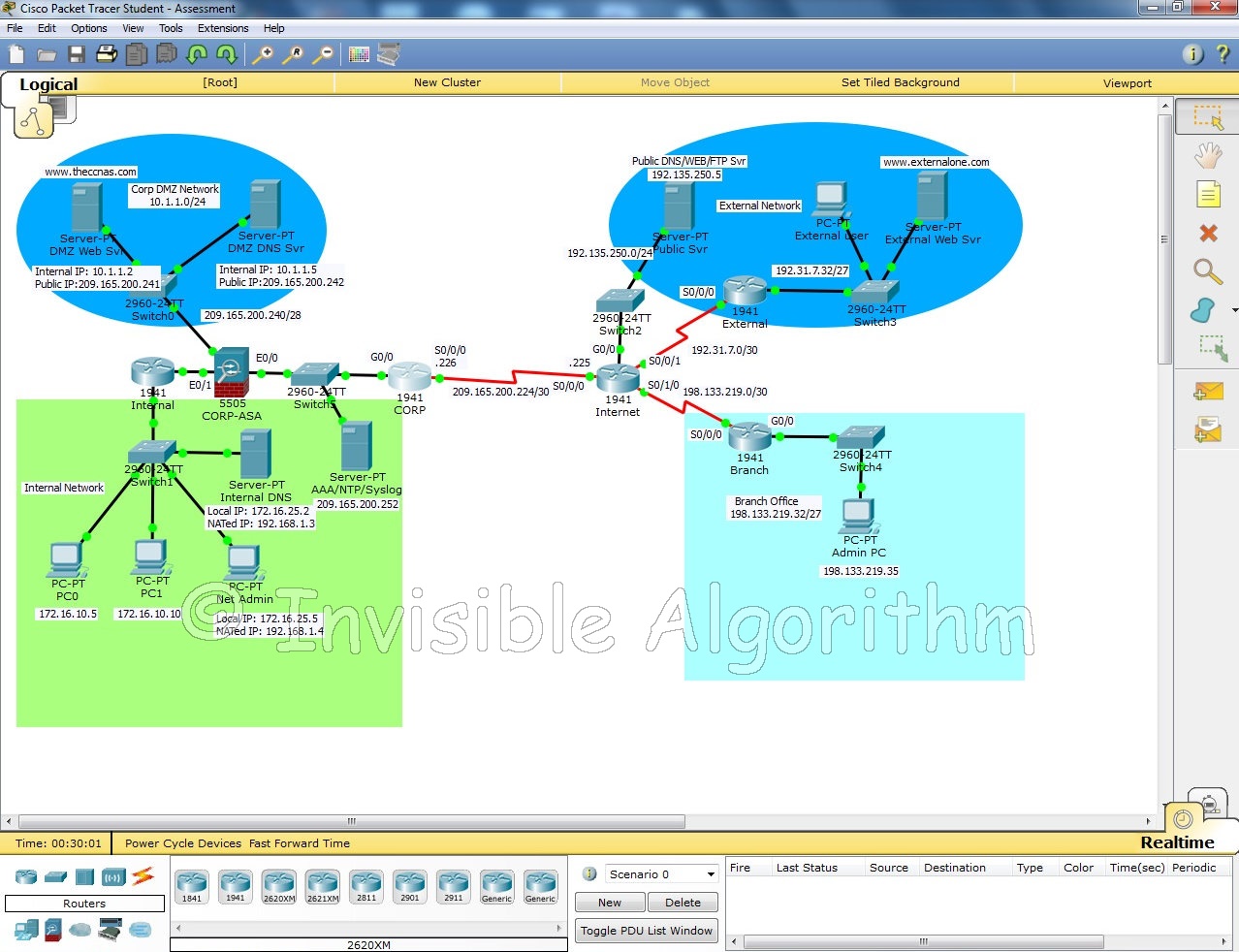
PDF) Packet Tracer -Configure Cisco Routers for Syslog, NTP, and SSH Operations (Instructor Version) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port | Jairo Salazar Rivas -
![CCNA Security v2] 2.6.1.3 Packet Tracer - Configure Cisco Routers for Syslog, NTP, and SSH Operations CCNA Security v2] 2.6.1.3 Packet Tracer - Configure Cisco Routers for Syslog, NTP, and SSH Operations](https://3.bp.blogspot.com/--xsog3hEPso/WyG-JoqsCoI/AAAAAAAABB0/5hVasmqVnIgt3e5UrOn6FU2qPhuprzIqQCLcBGAs/s1600/1.png)